If you’ve been following best practices, you likely have a multi-tiered Microsoft PKI with an offline root CA. In this case you’ll have to publish a new Certificate Revocation List using your offline CA server and install this on your online CA server. The following article outlines the steps involved in completing this process.
Generating the new CRL Using the Offline CA
First, you’ll need to power up your offline CA. Once it’s finished booting, navigate to C:\windows\system32\certsrv\certenroll and rename your current CRL (filename may vary, but should be the only file in this folder with a *.crl extension) to *.crl.old.
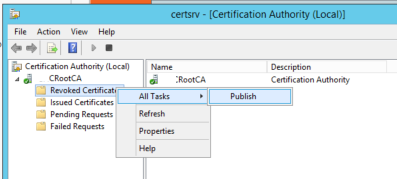
Read more →
We have a large number of network devices at work that are using our Domain Controllers for DNS resolution, RADIUS and DHCP. As well as a number of on premise systems which are binding to hostnames for LDAP authentication. Whilst it would totally be possible to go through all of these and change the configuration to use new servers, sometimes it’s just easier to replace the 2008R2 Domain Controllers with a new 2019 Domain Controller with the same hostname and IP address.
Read more →
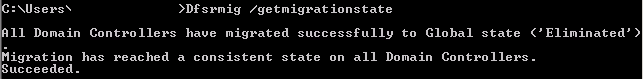
I’m sure with Microsoft announcing the End of Life of Server 2008R2 on January 14th 2020 many people are looking around and still seeing it all over the enterprise.
You may still be running domain controllers on 2008R2 which are using FRS for AD replication and are looking to move these to 2019 or similar and finding that it’s
unsupported until you’ve migrated your AD replication from FRS to DFSR.
If this is your situation, this guide should help you get them migrated over to DFSR. The method below provides for some rollback options if required, please see the full migration guide from Microsoft for more information. I’d recommend at least scanning through this document before you proceed with the steps below.
Read more →


